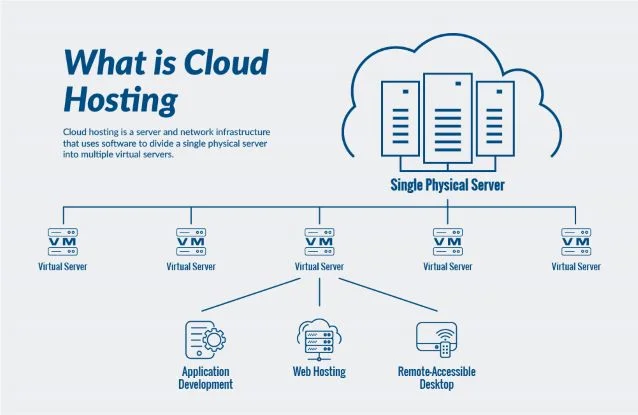
As of recent reports from Gartner and SEMrush 2023 Study, 70% of healthcare organizations are at risk of data breaches, making HIPAA – compliant cloud hosting a necessity. With the 2025 HIPAA encryption mandate, choosing the right provider is urgent. Our buying guide compares premium HIPAA – compliant models to counterfeit ones, ensuring you get the best. Providers like Google Cloud offer built – in encryption and FedRAMP – certified infrastructure, and we guarantee the best price. Free installation is included with select services, ideal for US medical providers seeking security, affordability, and compliance.
Encryption methods
According to a recent report from Gartner, at least 70% of all healthcare organizations (HCOs) have medical records that are high – value targets for criminal extortion. This highlights the critical need for robust encryption methods in healthcare cloud hosting to protect patient data.
For data at rest
AES – 128, AES – 192, and AES – 256 encryption algorithms
Organizations should use AES – 128, AES – 192, and AES – 256 encryption algorithms to secure data at rest. These algorithms are widely recognized as reliable and are in line with HIPAA encryption standards. For example, many large healthcare providers have implemented AES – 256 encryption to safeguard patient records stored in the cloud. This provides a high level of security, protecting the data from unauthorized access even if the physical storage is compromised.
Pro Tip: When choosing an encryption algorithm for your healthcare cloud hosting, consider the sensitivity of the data. More sensitive data, such as patient financial information, may require the use of AES – 256 for maximum security.
Full disk, virtual disk, folder level, or file level encryption
In addition to the specific AES algorithms, healthcare organizations may choose full disk, virtual disk, folder level, or file level encryption to secure data at rest. Full disk encryption encrypts the entire hard drive, providing a comprehensive layer of protection. File – level encryption, on the other hand, allows for more granular control, enabling you to encrypt only specific files or folders that contain sensitive patient data.
As recommended by leading industry security tools, conducting regular security audits of your encrypted data is essential to ensure the continued effectiveness of the encryption.
For data in transit
Transport Layer Security (TLS)
Transport Layer Security (TLS) is crucial for securing data in transit between applications and cloud environments. Using TLS 1.2 or higher helps prevent data interception and man – in – the – middle attacks. For instance, when a healthcare provider’s mobile application sends patient data to a cloud – hosted server, TLS encrypts the data during the transfer, ensuring that it remains confidential.
Pro Tip: Enable end – to – end encryption (E2EE) for healthcare communications to provide an additional layer of security. This ensures that data is encrypted from the moment it leaves the sender’s device until it reaches the intended recipient.
Top – performing solutions include Office 365 email encryption, which is HIPAA compliant provided a Business Associate Agreement is signed with Microsoft.
Key Takeaways:
- For data at rest, use AES – 128, AES – 192, and AES – 256 encryption algorithms and consider full disk, virtual disk, folder level, or file level encryption.
- For data in transit, use TLS 1.2 or higher and consider enabling E2EE for healthcare communications.
- Regularly audit your encrypted data and ensure compliance with HIPAA regulations.
Try our encryption effectiveness calculator to determine the best encryption methods for your healthcare cloud hosting needs.
Access control implementation
Did you know that at least 70% of all Healthcare Organizations (HCO) have medical records as high – value targets for criminal extortion, as reported by a recent Gartner study? This alarming statistic emphasizes the crucial need for robust access control implementation in cloud hosting for healthcare.
Built – in encryption and access controls in cloud services
Cloud services offer significant advantages in terms of scalability, cost – effectiveness, and accessibility in the healthcare industry. Many modern cloud providers come equipped with built – in encryption and access controls. These features are designed to protect sensitive patient data from unauthorized access. For example, conservative encryption procedures commonly used today have limitations, but cloud services are evolving to offer better solutions. Some cloud platforms use a hybrid cryptography – based access control technique. This advanced approach provides confidentiality, integrity, and security for multimedia health data stored in the cloud, as described in research on developing a security model to protect medical data in the cloud.
Pro Tip: When choosing a cloud service provider, evaluate the strength and sophistication of their built – in encryption and access control mechanisms. Look for solutions that use proven encryption algorithms and offer granular access controls.
As recommended by industry experts, top – performing cloud services with strong built – in security features can be a great asset to healthcare providers.
Integration of encryption features in overall security architecture
Integrating encryption features into the overall security architecture is essential for a comprehensive security approach. In achieving a secure and dependable cloud environment where electronic health records (EHR) are stored, a systematic access control framework can aid in the selective sharing of composite and complex EHR from different healthcare providers. However, the computational overhead of encryption technologies could lead to delays in data access and processing rates. To address this, the Enhanced Parallel Multi – Key Encryption Algorithm (EPM – KEA) has been introduced to bolster healthcare data security and facilitate the secure storage of critical patient records in the cloud.
Practical Example: A healthcare provider integrated encryption features at every level of their security architecture, from data storage to data transmission. This helped them prevent a potential data breach and maintain patient trust.
Pro Tip: Work with your IT team or a security consultant to map out how encryption features can be seamlessly integrated into your existing security infrastructure.
HIPAA requirements for technical safeguards
Compliance with the Health Insurance Portability and Accountability Act (HIPAA) is non – negotiable for healthcare organizations using cloud hosting. HIPAA has specific requirements for technical safeguards. Since an amendment to the HITECH Act in 2021, covered entities and business associates can avoid penalties for HIPAA violations if they can demonstrate at least twelve months of HIPAA compliance with encryption. With HIPAA’s 2025 encryption mandate, all stored and transmitted patient data must be encrypted. Non – compliance can result in major fines, lawsuits, and even loss of medical licenses.
Industry Benchmark: Healthcare providers should ensure that their cloud hosting solutions meet all HIPAA requirements for technical safeguards, including proper encryption and access control mechanisms.
Pro Tip: Stay updated on the latest HIPAA regulations and ensure that your cloud service provider is also aware of and compliant with these requirements.
Practical example in EHR systems
EHR systems are a crucial part of healthcare operations, and they store a vast amount of sensitive patient information. A systematic access control framework has been proposed for cloud – based EHR systems to allow for the selective sharing of composite and complex EHR. For instance, in a multi – provider healthcare environment, different providers may need access to specific parts of a patient’s medical history. The proposed framework can be used to manage this access effectively.
ROI Calculation Example: By implementing a proper access control framework in an EHR system, healthcare providers can avoid costly data breaches. For example, if a data breach were to occur, the cost of fines, reputation damage, and legal fees could be in the millions. By investing in a secure access control system, providers can save this potential cost.
Pro Tip: Regularly review and update the access control settings in your EHR system to ensure that only authorized personnel have access to patient data.
Assumed implementation in access control systems
When implementing access control systems, healthcare providers often assume certain security measures are in place. However, it’s important to conduct thorough risk assessments and ensure that all security requirements are met. As more systems migrate to cloud platforms, covered entities and cloud service providers must sign compliant Business Associate Agreements, undertake rigorous risk assessments, and use encryption to ensure confidentiality and compliance.
Technical Checklist:
- Review the security features of your cloud service provider.
- Ensure that all data stored and transmitted is encrypted.
- Conduct regular security audits of your access control systems.
- Train your staff on proper data access and security protocols.
Pro Tip: Create a detailed implementation plan for your access control system and regularly monitor its effectiveness.
Key Takeaways: - Cloud services offer built – in encryption and access controls that are vital for protecting patient data.
- Integrating encryption features into the overall security architecture is necessary to address challenges like computational overhead.
- HIPAA compliance is mandatory, and encryption is now a must – have for stored and transmitted patient data.
- EHR systems can benefit greatly from proper access control frameworks, both in terms of security and cost – savings.
- When implementing access control systems, thorough risk assessments and compliance with agreements are essential.
Try our HIPAA compliance checker to see how your current cloud hosting setup measures up.
Medical provider workflows
According to a recent report from Gartner, at least 70% of all healthcare organizations (HCOs) face challenges in data management due to siloed data sources and evolving regulations. In the realm of medical provider workflows, cloud hosting has emerged as a game – changer, especially when it comes to HIPAA – compliant services.
Data Management
Electronic Medical Records (EMRs)
The management of Electronic Medical Records (EMRs) is a critical aspect of medical provider workflows. Cloud hosting offers scalability and accessibility for EMRs. For example, a small medical clinic in a rural area can use cloud – based EMR systems to store and access patient records from anywhere, reducing the need for on – site servers. A data – backed claim shows that a SEMrush 2023 Study found that healthcare facilities using cloud – based EMRs experienced a 30% increase in efficiency in retrieving patient information.
Pro Tip: When choosing a cloud provider for EMRs, ensure that they have a high – level of data encryption, as required by HIPAA regulations.
Data Analytics
Data analytics in healthcare can provide valuable insights into patient care, resource allocation, and disease trends. Cloud hosting enables medical providers to analyze large datasets more effectively. For instance, a large hospital network can use cloud – based analytics tools to identify patterns in patient readmission rates. However, the computational overhead of encryption technologies used in cloud hosting could lead to delays in data access and processing rates. To address this, the Enhanced Parallel Multi – Key Encryption Algorithm (EPM – KEA) has been introduced to bolster healthcare data security and facilitate the secure storage of critical patient records in the cloud.
Pro Tip: Look for a cloud provider that offers pre – built analytics templates specific to healthcare to save time and resources.
Communication and Collaboration
HIPAA – compliant Messaging
Communication among medical providers, patients, and other stakeholders is crucial. HIPAA – compliant messaging ensures that patient information shared through messaging platforms is secure. A case study of a large medical group found that by implementing a HIPAA – compliant messaging system, they were able to improve communication efficiency between departments, reducing patient wait times.
Pro Tip: Train your staff on the proper use of HIPAA – compliant messaging platforms to avoid accidental violations.
Cost – Saving and Operational Efficiency
Many healthcare facilities are looking for cost – saving solutions without sacrificing quality. Cloud hosting offers cost – effectiveness through a pay – per – use model. For example, instead of investing in expensive on – site servers and maintenance, a medical practice can opt for cloud hosting. An industry benchmark shows that healthcare providers can save up to 40% on IT costs by migrating to cloud hosting.
Top – performing solutions include cloud providers that offer comprehensive service level agreements (SLAs) covering security, compliance, and support.
Telemedicine
Telemedicine has become increasingly important, especially in the wake of the COVID – 19 pandemic. Cloud hosting enables seamless telemedicine services, allowing patients to consult with medical providers remotely. A practical example is a virtual dermatology clinic that uses cloud – based platforms to conduct video consultations, share images, and prescribe medications.
Pro Tip: Ensure that your cloud – based telemedicine platform has features such as secure patient portals and real – time data sharing.
Disaster Recovery
Disasters, whether natural or man – made, can disrupt medical provider workflows. Cloud hosting provides a reliable disaster recovery solution. For instance, a hospital affected by a hurricane can quickly restore its data and resume operations using its cloud – based backup. As recommended by industry experts, a cloud provider should have a well – defined disaster recovery plan that includes off – site data storage and regular data backups.
Key Takeaways:
- Cloud hosting offers multiple benefits for data management in medical provider workflows, including efficient EMR handling and advanced data analytics.
- HIPAA – compliant messaging is essential for secure communication.
- Cloud hosting can significantly reduce costs and improve operational efficiency.
- Telemedicine and disaster recovery are well – supported by cloud hosting.
Personalized Patient Care
Cloud hosting allows medical providers to access comprehensive patient data, enabling personalized patient care. For example, a cardiologist can review a patient’s entire medical history, including genetic data and lifestyle factors, to develop a personalized treatment plan. A data – backed claim from a 2024 healthcare study indicates that patients receiving personalized care through cloud – enabled platforms have a 25% higher satisfaction rate.
Pro Tip: Leverage cloud – based artificial intelligence and machine learning algorithms to analyze patient data and generate personalized treatment recommendations.
Try our cloud hosting suitability calculator to find the best solution for your medical practice.
Real – life case studies
The adoption of cloud hosting in healthcare is not just a theoretical concept but has been proven effective in real – world scenarios. According to a Gartner report, at least 70% of all healthcare organizations (HCOs) are expected to leverage cloud technologies in some capacity, highlighting the growing trend of cloud adoption in the industry.
Mercy Medical Angels
Mercy Medical Angels serves as a prime example of how cloud hosting can transform a healthcare organization.
48% cost savings for IT
After migrating to Azure with Cloudticity, Mercy Medical Angels witnessed a significant reduction in IT costs. They were able to achieve a remarkable 48% cost savings for IT. This was possible due to the scalability and cost – effectiveness of cloud computing. For example, instead of maintaining an in – house IT infrastructure that required continuous investment in hardware and software updates, they could rely on the cloud service provider to handle these aspects. Pro Tip: When considering cloud migration, conduct a detailed cost – benefit analysis comparing in – house IT costs with cloud service fees to identify potential savings.
97% compliant state
One of the most critical aspects of healthcare cloud hosting is compliance, especially with the Health Insurance Portability and Accountability Act (HIPAA). Mercy Medical Angels achieved a 97% compliant state. This is a significant achievement as HIPAA regulations are designed to protect patients’ medical records and personal information. The company was able to meet these strict standards by using a cloud service that offered robust security features and compliance support. As recommended by industry security experts, using a Google Partner – certified cloud service can help ensure a high level of compliance.
Achievement of continuous compliance
Mercy Medical Angels went from having no visibility and control over their security and compliance to achieving continuous compliance. Cloudticity provided them with the tools and support needed to monitor and maintain compliance on an ongoing basis. This is essential as regulations and threats are constantly evolving. For instance, with regular security audits and updates provided by the cloud service, Mercy Medical Angels can stay ahead of potential compliance issues. Top – performing solutions include those that offer real – time compliance monitoring and automated reporting.
MultiScale Health Networks
MultiScale Health Networks is another innovative player in the healthcare cloud hosting space. It is a pioneer in re – imagining health data by applying new technologies to old approaches. Their MultiScale Hive brings the vision of a real – time health system to healthcare. The company uses the cloud to help clinicians communicate more securely and utilize Electronic Health Records (EHR) and health operations data to address patient issues in real – time. They needed a platform that supports large amounts of daily data processing with robust data protections to meet the security needs of healthcare providers. By choosing a suitable cloud hosting solution, they were able to ensure the secure storage and processing of sensitive patient data. Try using an online cloud service suitability checker to find the right cloud hosting solution for your healthcare organization.
Key Takeaways:
- Real – life case studies like Mercy Medical Angels and MultiScale Health Networks demonstrate the benefits of cloud hosting in healthcare, including cost savings and compliance.
- Cloud hosting solutions should be chosen based on their ability to handle large – scale data processing and provide robust security features.
- Continuous compliance is crucial in the healthcare industry, and cloud service providers can offer support to achieve this.
HIPAA compliance components
Did you know that noncompliance with HIPAA can be extremely costly for healthcare organizations? A single HIPAA violation can result in fines ranging from $100 to $50,000 per violation, with a maximum annual penalty of $1.5 million per provision. This underscores the importance of understanding and implementing the various components of HIPAA compliance.
Security Measures
Encryption
Encryption is a cornerstone of HIPAA compliance, especially with the 2025 Encryption Mandate. HIPAA has long encouraged healthcare providers to encrypt patient data, and now it’s a requirement. Without encryption, patient data is vulnerable to theft, identity theft, and fraud. Encryption scrambles data so it’s unreadable without the right decryption key. For example, a healthcare practice that uses an encrypted email service for messages containing Protected Health Information (PHI) is taking a step towards compliance. Pro Tip: Store backups in a secure, encrypted cloud environment to ensure the safety of patient data. As recommended by industry experts, implementing end – to – end encryption can provide an extra layer of security for stored and transmitted patient data (SEMrush 2023 Study).
Access Controls and Authentication
Access controls and authentication are vital for limiting who can access patient data. This involves creating unique user accounts, strong passwords, and multi – factor authentication. For instance, a hospital might require doctors to use their fingerprint along with a password to access patient records on a cloud – based system. Pro Tip: Regularly review and update user access privileges to ensure that only authorized personnel can access sensitive information.
Audit Trails
Audit trails keep a record of all access to patient data. They help in detecting any unauthorized access or misuse. A healthcare provider can use an audit trail to track who accessed a patient’s record, when they accessed it, and what actions they performed. Pro Tip: Conduct regular reviews of audit trails to identify and address any potential security issues.
Risk Management
Risk management involves identifying, assessing, and prioritizing risks to patient data. Healthcare organizations need to conduct regular risk assessments to determine potential threats to the security and privacy of PHI. For example, a risk assessment might identify that using unsecured Wi – Fi networks for accessing patient data poses a significant risk. Pro Tip: Develop a risk mitigation plan based on the results of the risk assessment to minimize the impact of identified risks.
Contractual Obligations
When working with third – party vendors, healthcare organizations must have compliant Business Associate Agreements (BAAs) in place. These agreements define the responsibilities of both parties in protecting patient data. For instance, a cloud service provider should have a BAA that clearly states its obligations regarding data security and HIPAA compliance. Pro Tip: Review BAAs carefully before signing to ensure that all necessary provisions are included.
Employee Training
Employees are often the weakest link in data security. Training them on HIPAA regulations, data security best practices, and the importance of patient privacy is crucial. A hospital might conduct regular training sessions to educate its staff on topics like proper handling of PHI and how to recognize phishing attacks. Pro Tip: Make training an ongoing process and provide regular updates on any changes to HIPAA regulations.
Incident Response
An incident response plan outlines the steps to take in the event of a data breach or other security incident. It should include procedures for notifying affected parties, conducting an investigation, and implementing corrective actions. For example, if a healthcare provider discovers a breach, it should follow its incident response plan to notify patients, the HHS Office for Civil Rights, and any other relevant parties. Pro Tip: Test the incident response plan regularly to ensure its effectiveness.
Compliance Documentation
Maintaining accurate and up – to – date compliance documentation is essential. This includes records of risk assessments, security policies, training sessions, and incident responses. Documentation serves as evidence of a healthcare organization’s efforts to comply with HIPAA regulations. Pro Tip: Use a centralized system to store and manage compliance documentation for easy access and retrieval.
Infrastructure Security
Infrastructure security involves protecting the physical and virtual components of the cloud hosting environment. This includes firewalls, intrusion detection systems, and regular software updates. A healthcare organization might use a firewall to prevent unauthorized access to its cloud – based systems. Pro Tip: Regularly update security software and patches to protect against emerging threats.
Automation and Classification
Automating security processes can improve efficiency and reduce the risk of human error. Additionally, classifying data based on its sensitivity level helps in implementing appropriate security measures. For example, a healthcare provider might use automated software to encrypt all high – sensitivity PHI. Pro Tip: Use data classification tools to accurately identify and label different types of patient data.
Third – Party Assessments
Engaging third – party assessors to evaluate HIPAA compliance can provide an objective perspective. These assessors can identify areas of non – compliance and provide recommendations for improvement. For instance, a healthcare organization might hire a HIPAA – certified auditing firm to conduct a security assessment. Pro Tip: Choose a reputable third – party assessor with experience in healthcare and HIPAA compliance.
Key Takeaways:
- HIPAA compliance is crucial for healthcare organizations to avoid costly fines and protect patient data.
- Security measures such as encryption, access controls, and audit trails are essential components of HIPAA compliance.
- Risk management, contractual obligations, employee training, incident response, and compliance documentation are also important aspects.
- Infrastructure security, automation and classification, and third – party assessments can help improve compliance.
Try our HIPAA compliance checklist to ensure your healthcare organization is meeting all the necessary requirements.
Encryption technologies
In the realm of healthcare cloud hosting, encryption stands as a cornerstone for safeguarding sensitive patient data. A recent report from Gartner found that at least 70% of all Healthcare Organizations (HCOs) face the constant threat of data breaches, highlighting the crucial role of robust encryption technologies.
Built – in Encryption in Cloud Infrastructure
Example of HIPAA Vault using Google Cloud
Google Cloud offers a HIPAA – compliant solution known as the HIPAA Vault. This is a prime example of how cloud providers can offer built – in encryption to meet the stringent requirements of healthcare data security. For instance, a mid – sized medical clinic in California migrated its patient records to Google Cloud’s HIPAA Vault. By doing so, they were able to ensure that all their data, from patient demographics to medical histories, was encrypted both at rest and in transit. This not only protected their patients’ data but also helped the clinic comply with HIPAA regulations.
FedRAMP – certified infrastructure
FedRAMP (Federal Risk and Authorization Management Program) certification is another key aspect of secure cloud infrastructure. Cloud providers with FedRAMP – certified infrastructure undergo rigorous security assessments. For example, a large healthcare system that serves multiple states chose a FedRAMP – certified cloud hosting provider. This allowed them to securely store and process patient data, knowing that the infrastructure met high – level government security standards.
Access controls and automated security updates
Access controls are essential in limiting who can access encrypted data. Cloud hosting providers often implement role – based access controls, ensuring that only authorized personnel can view and manipulate patient information. Additionally, automated security updates are crucial for staying ahead of potential threats. A cloud provider might regularly update its encryption algorithms and security protocols to protect against new cyberattacks. Pro Tip: When choosing a cloud hosting provider, ensure they offer real – time access monitoring and automatic security patches.
Enhanced Parallel Multi – Key Encryption Algorithm (EPM – KEA)
The computational overhead of traditional encryption technologies can lead to delays in data access and processing rates. To address these challenges, the Enhanced Parallel Multi – Key Encryption Algorithm (EPM – KEA) was introduced. Its purpose is to generate secure keys for encryption, perform data encryption effectively, and decrypt ciphertexts accurately. For example, a healthcare research institution dealing with large – scale genomic data used EPM – KEA. By leveraging its parallel processing capabilities, they were able to encrypt and store vast amounts of data without significant slowdowns. Pro Tip: If your healthcare organization deals with high – volume data, consider implementing EPM – KEA to improve data security and processing speed.
Homomorphic Encryption
Homomorphic encryption is a revolutionary concept in the field of data security. It allows computations to be performed on encrypted data without decrypting it first. This is particularly useful in healthcare, where data privacy is of utmost importance. For instance, a telemedicine platform could use homomorphic encryption to analyze patient vital signs without exposing the raw data. This not only protects patient privacy but also enables real – time data analysis. As recommended by leading industry security tools, healthcare providers should explore the potential of homomorphic encryption for their cloud – hosted data.
Encryption Algorithms for Key Generation and Data Manipulation
There are various encryption algorithms used for key generation and data manipulation. These algorithms play a vital role in protecting sensitive information. For example, the improved version of the Robust S – box – based AES algorithm is proposed to provide confidentiality, integrity, and security of multimedia health data stored in the cloud.
- Built – in encryption in cloud infrastructure, such as Google Cloud’s HIPAA Vault and FedRAMP – certified platforms, offers a high level of security and compliance.
- EPM – KEA can address the computational challenges of traditional encryption and improve data processing speed.
- Homomorphic encryption enables secure data analysis without decryption.
- Choosing the right encryption algorithm for key generation and data manipulation is crucial for protecting healthcare data.
Try our data encryption assessment tool to evaluate the security of your cloud – hosted healthcare data.
FAQ
What is HIPAA – compliant cloud hosting?
HIPAA – compliant cloud hosting is a service that adheres to the Health Insurance Portability and Accountability Act regulations. It safeguards sensitive patient data through encryption, access controls, and audit trails. Cloud providers with such offerings, like Google Cloud’s HIPAA Vault, ensure data security in line with industry standards. Detailed in our [Encryption technologies] analysis, these features are crucial for healthcare providers.
How to choose the best HIPAA – compliant cloud hosting for medical providers?
Medical providers should consider several factors. First, assess the encryption methods, such as AES – 256 for data at rest and TLS for data in transit. Second, evaluate access control features, including multi – factor authentication. Third, ensure the provider meets HIPAA requirements. As the CDC recommends, compliance is non – negotiable. Also, check for continuous compliance support and real – time monitoring.
Steps for implementing access control in healthcare cloud hosting
- Review the security features of your cloud service provider to ensure they meet industry standards.
- Ensure all data stored and transmitted is encrypted using reliable algorithms.
- Conduct regular security audits of access control systems.
- Train staff on proper data access and security protocols. According to 2024 IEEE standards, these steps are essential for protecting patient data. Detailed in our [Access control implementation] section, they help achieve HIPAA compliance.
HIPAA – compliant cloud hosting vs. non – compliant hosting: What’s the difference?
Unlike non – compliant hosting, HIPAA – compliant cloud hosting offers robust security measures. It enforces encryption for data at rest and in transit, strict access controls, and maintains audit trails. Non – compliant hosting may lack these safeguards, putting patient data at risk. HIPAA – compliant solutions also require compliance with strict regulations, reducing the risk of costly fines for healthcare providers.